Summarize the Content of the Blog
Key Takeaways
Cut alert noise by 90%: Risk-Based Alerting in Splunk ES eliminates false positives and surfaces real threats
Respond in minutes, not hours: Automated playbooks in Splunk SOAR contain threats before they spread
Work smarter, not harder: One analyst with automation handles more incidents than a team doing manual work
Get complete visibility: Combine security events with infrastructure monitoring to catch threats others miss
Start fast, scale smart: Begin with high-impact use cases and expand as you see results
Imagine this: It's 3 AM, and your security analyst gets paged about a potential breach. She logs into five different systems, manually checks threat feeds, correlates user behavior, and two hours later discovers it was a false alarm. Meanwhile, real threats are buried in thousands of unreviewed alerts.
This is the reality for most security teams today. They're drowning in alerts, juggling disconnected tools, and spending most of their time on repetitive tasks instead of hunting actual threats.
The solution? A unified Splunk security operations pipeline that connects detection, investigation, and automated response into one seamless workflow.
Why Traditional Security Operations Aren't Working
Most security teams today face the same problems:
Alert overload: Your SIEM generates thousands of alerts daily. Most are false positives, but your team has to investigate each one to find the real threats buried in the noise.
Tool sprawl: Analysts switch between multiple consoles—SIEM, endpoint protection, threat intelligence, ticketing systems—losing context and wasting time during critical investigations.
Manual response: When a threat is confirmed, analysts manually execute response steps across different tools. By the time they quarantine an infected system or block a malicious sender, the damage is often done.
Burned-out teams: Your best security talent spends 70% of their time on repetitive tasks that should be automated. They're exhausted, and retention is suffering.
The problem isn't lack of technology—it's lack of integration. Disconnected tools create friction that slows detection and response, giving attackers the time they need to cause serious damage.
The Three Stages of a Complete Security Pipeline
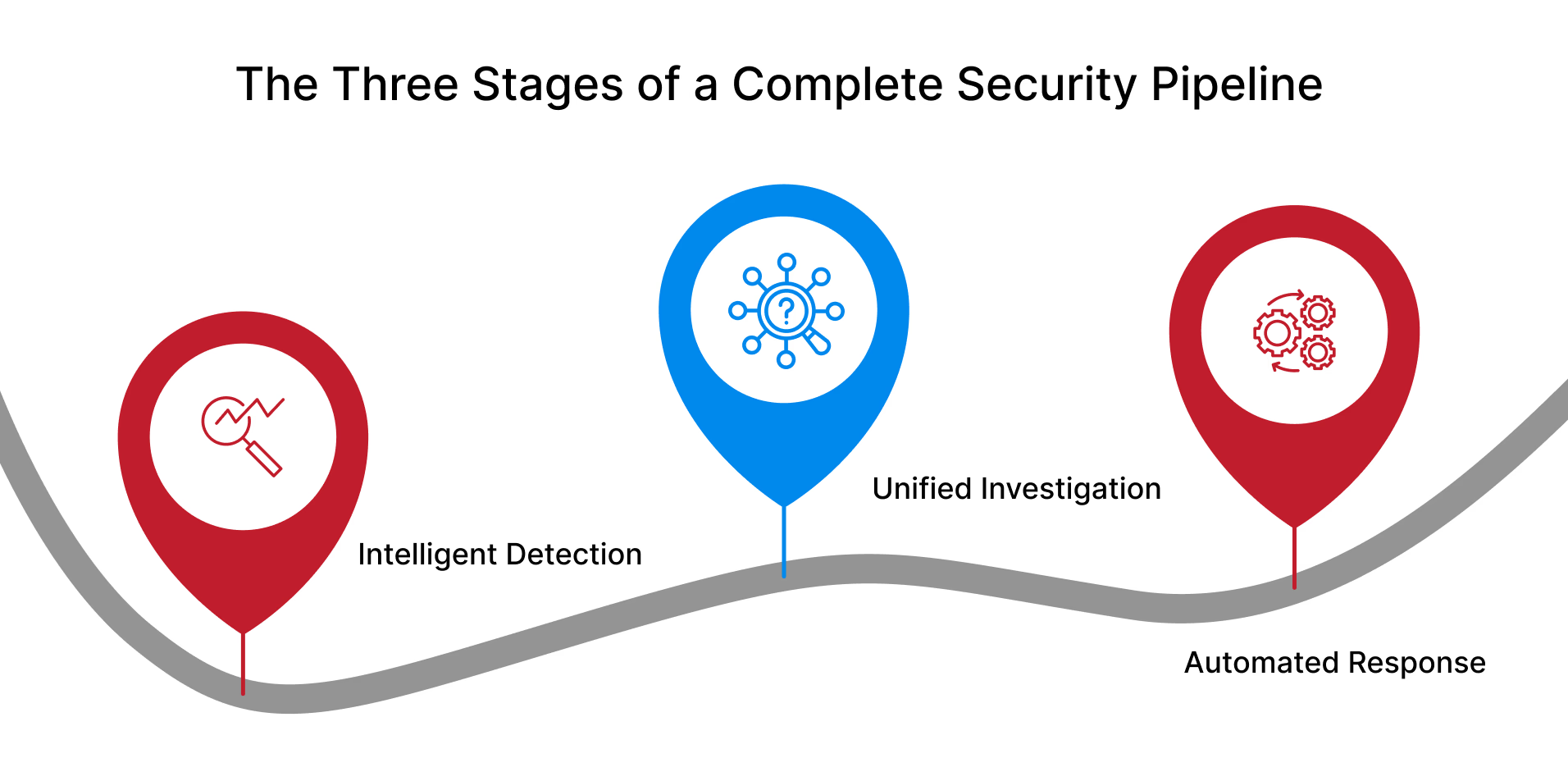
A mature security operations pipeline connects three critical stages:
1. Intelligent Detection
Instead of alerting on every anomaly, use risk-based analytics to identify real threats. Multiple low-confidence signals combine into high-confidence alerts, dramatically reducing noise.
2. Unified Investigation
When a threat is detected, all relevant context—user behavior, threat intelligence, related events—appears automatically in one interface. No more hunting through multiple systems.
3. Automated Response
Pre-defined playbooks execute proven response procedures across all your security tools simultaneously. Threats get contained at machine speed while analysts stay informed.
Stage 1: Smart Detection with Splunk Enterprise Security
Splunk Enterprise Security (ES) is your centralized brain for threat detection. It collects data from across your entire environment—firewalls, endpoints, cloud services, applications—and uses advanced analytics to find real threats.
Risk-Based Alerting: The Game Changer
Traditional SIEMs create an alert for every suspicious event. If a user logs in from a new location, that's an alert. If they access a file after hours, another alert. Each requires a separate investigation.
Splunk Enterprise Security works differently. It assigns risk scores to users and systems based on their behavior. That unusual login? +20 points. After-hours file access? +30 points. Large data download? +50 points. Only when the total risk exceeds your threshold does ES create one comprehensive alert with full context.
This is how organizations reduce alert fatigue Splunk ES SOAR style—cut volume by 90% while improving accuracy.
Behavioral Analytics That Catch What Rules Miss
ES includes User and Entity Behavior Analytics (UEBA) that learns normal patterns for every user and device. When someone's behavior changes significantly—like an accountant suddenly accessing HR systems at 2 AM from a foreign IP—UEBA flags it even if the attacker has valid credentials.
This catches insider threats, compromised accounts, and advanced attacks that evade traditional signature-based detection.
Built-In Threat Intelligence
ES automatically enriches your alerts with threat intelligence from multiple sources. Investigating a suspicious IP? You instantly see if it's linked to known threat actors, what tactics they use, and how severe the threat is—no manual lookups needed.
Stage 2: Automated Response with Splunk SOAR
Detection means nothing if the response is slow. Splunk SOAR (Security Orchestration, Automation, and Response) turns hours of manual work into minutes of automated action.
How Playbook Automation Works
SOAR connects to all your security tools—email gateways, firewalls, endpoint protection, cloud platforms—and orchestrates response actions across all of them through pre-built playbooks.
Example: Phishing Response Automation
Your team handles 50+ phishing reports weekly. Each one takes 2-3 hours of manual work: finding all copies of the email, quarantining them, extracting malicious URLs, blocking the sender, resetting credentials for users who clicked links, and documenting everything.
With automated incident response, Splunk SOAR provides one playbook that handles it all automatically in under two minutes. Your analyst just reviews the results instead of executing 20 manual steps. That's how one person can handle more incidents than an entire team doing manual work.
Native Integration with Splunk ES
Here's where Splunk ES SOAR integration becomes powerful: response actions happen directly within your investigation workflow. When investigating an alert in ES, analysts see available playbooks and can execute them without switching tools. All results are automatically documented in the case timeline.
With ES 8.0 and SOAR 6.3, this integration is native—not a bolt-on connector. Detection, investigation, and response happen in one unified experience.
Start Semi-Automated, Scale to Full Automation
You don't have to automate everything immediately. Start with playbooks that gather information and suggest actions. Analysts review and approve before execution. Once you're confident, enable full automation for routine tasks while keeping manual approval for high-impact actions like system isolation.
Stage 3: Extended Visibility with Splunk Observability Cloud
Some threats don't show up in security logs. A sudden CPU spike might be crypto mining malware. Memory consumption anomalies could indicate malicious code execution. Network throughput changes might signal data theft.
Splunk Observability Cloud monitors your infrastructure and applications in real-time. When this operational data feeds into ES, performance anomalies become security signals.
Real example: A production Kubernetes cluster shows elevated CPU usage. DevOps thinks it's a capacity issue. But when observability metrics correlate with security events in ES—containers communicating with unknown IPs, no increase in legitimate application load, the picture becomes clear: compromised containers mining cryptocurrency.
Traditional security logs missed it. Observability data caught it. This is the power of Splunk Cloud threat management with complete visibility.
How to Build Your Pipeline: A Practical Roadmap
Month 1-2: Foundation
- Connect your key data sources to Splunk ES (firewalls, endpoints, cloud logs)
- Configure Risk-Based Alerting for your top 3-5 threat types
- Set up SOAR integrations with your most-used tools (email, endpoint, identity)
- Build 1-2 playbooks for your highest-volume incidents (usually phishing)
Month 3-4: Expansion
- Add more data sources for broader coverage
- Fine-tune risk scoring to reduce remaining false positives
- Create 3-5 additional playbooks for common scenarios
- Train your team on the new workflows
Month 5-6: Optimization
- Measure results and adjust based on what you learn
- Enable UEBA for behavioral threat detection
- Integrate observability data for complete visibility
- Plan your next wave of automation
Implementation Note: Implementation timelines are estimates and vary based on your organization's specific environment, data sources, and requirements. Contact bitsIO for a personalized assessment and timeline.
When to Use Managed Services
Many teams lack the Splunk expertise needed to build this quickly. Splunk managed services How to Build Your Pipeline: A Practical Roadmap
provider handles the configuration, tuning, playbook development, and ongoing optimization—so you can get results fast without hiring specialists.
Organizations using managed services see value x50% faster and avoid common mistakes that require expensive rework. If you're migrating to Splunk Cloud or need to scale without adding headcount, managed services make sense.
Ready to Transform Your Security Operations?
If your team is drowning in alerts and spending more time on manual tasks than hunting threats, it's time for a change.
bitsIO specializes in building complete Splunk security operations pipelines. Our certified experts help you design, implement, and optimize integrated ES and SOAR solutions tailored to your environment. We handle the heavy lifting—configuration, playbook development, tuning—so you see results fast without hiring specialists.
Most clients achieve measurable improvements within 60 days: 90% fewer alerts, sub-two-minute response times, and security operations that scale without constant hiring.
Take the Next Step
Schedule a 30-minute consultation with our Splunk security team. We'll discuss your current challenges, show you what's possible, and provide a clear roadmap—no pressure, no obligation.
Book Your Free Consultation Now















