Summarize the Content of the Blog
Key Takeaways
Ransomware attacks on industrial operators surged 46% from Q4 2024 to Q1 2025, with manufacturing bearing 65% of all OT-targeted incidents [1]
Unplanned downtime from cyber incidents costs Fortune 500 companies approximately $1.5 trillion annually, representing 11% of their revenue [1]
52% of organizations now place OT security under the CISO, up from just 16% in 2022, signaling a strategic shift in how industrial cybersecurity is managed [2]
Unified OT-SIEM platforms like Splunk enable real-time threat detection across both IT and OT environments, breaking down traditional silos that leave critical infrastructure vulnerable
Network segmentation, asset visibility, and AI-driven threat detection form the cornerstone of modern OT security monitoring strategies
The industrial landscape has fundamentally changed. What was once physically isolated on factory floors—programmable logic controllers (PLCs), supervisory control and data acquisition (SCADA) systems, and distributed control systems (DCS)—is now digitally connected, internet-accessible, and increasingly targeted by sophisticated threat actors.
The convergence of Information Technology (IT) and Operational Technology (OT) has unlocked unprecedented efficiency and innovation. But it has also created a massive attack surface that traditional security approaches simply cannot protect. When a ransomware group can encrypt not just your financial records but your entire production line, the stakes aren’t measured in data loss—they’re measured in lives, supply chains, and critical infrastructure stability.
The Modern OT Threat Landscape: No Longer “Air-Gapped”
For decades, industrial control systems operated under a comforting assumption: physical isolation equals security. The so-called gap, or technically the firewall between operational technology (OT) and the IT environment, was supposed to be an impenetrable defense.
That assumption is dead.
Today’s ICS environments are deeply interconnected with enterprise networks, cloud platforms, remote access tools, and third-party vendor systems. The 2025 OT threat landscape is characterized by several alarming trends:
- Ransomware actors have shifted from opportunistic to strategic targeting. Groups like Qilin, Akira, and Play are specifically hunting industrial operators, exploiting OT-specific vulnerabilities in SCADA systems, historians, and industrial gateways. In Q2 2025 alone, 657 ransomware incidents impacted industrial entities worldwide, with manufacturing accounting for 428 of those attacks [3].
- The convergence of IT and OT creates hybrid attack vectors. Threat actors no longer need to breach the factory floor directly. They compromise the enterprise network first, pivot through poorly segmented connections, and land in the OT environment where legacy systems lack modern security controls. This IT-to-OT lateral movement is now the dominant attack pattern.
- Nation-state actors are weaponizing ransomware for geopolitical objectives. The line between cybercriminals and state-sponsored groups continues to blur. In March 2025, North Korea’s Moonstone Sleet group adopted Qilin ransomware operationally, signaling that OT attacks are no longer purely financial—they’re instruments of disruption and influence [3].
- Legacy systems remain fundamentally vulnerable. Many industrial environments still run Windows XP, unpatched SCADA software, and PLCs with hardcoded credentials. These systems were never designed with cybersecurity in mind, and retrofitting protection is technically complex and operationally risky. Also, most importantly, with the end of Windows 10 Support, this becomes an increasing concern.
The result? 31% of manufacturers experienced financial impacts from cyberattacks affecting OT/IT systems in 2024, including direct production stoppages [4]. When production stops, the costs compound exponentially—lost revenue, regulatory penalties, reputational damage, and in worst-case scenarios, safety incidents.
Why Traditional Security Tools Fall Short in OT Environments
Standard IT security solutions—firewalls, endpoint detection, traditional SIEM platforms—were built for data centers and corporate networks. They operate on assumptions that simply don’t hold in operational technology:
- Uptime is non-negotiable: OT systems often can’t be taken offline for patching or security scans. A manufacturing line running 24/7 can’t tolerate the downtime required for traditional security maintenance.
- Protocols are fundamentally different: OT networks use specialized industrial protocols (Modbus, DNP3, OPC, Profinet) that traditional security tools don’t understand. Without deep protocol inspection, threats sail past undetected.
- Context matters more than anomalies: In IT, unusual network traffic might indicate a threat. In OT, unusual behavior might be normal operations responding to production demands. Without operational context, security tools generate false positives that erode trust.
This is where specialized OT security monitoring becomes mission-critical—and why platforms like Splunk, when properly implemented, transform visibility across the entire industrial ecosystem.
The Role of Splunk in OT Security Monitoring
Splunk has evolved far beyond its origins as a log aggregation platform. Today, it serves as the nervous system for industrial security operations, providing unified visibility across IT and OT environments that legacy SIEM solutions simply cannot match.
Breaking Down the IT-OT Divide
The fundamental challenge in modern industrial cybersecurity isn’t just detecting threats—it’s correlating data across environments that have historically operated in complete isolation. IT teams monitor enterprise networks. OT teams focus on production systems. Security teams try to protect both but lack a unified view.
Splunk solves this by ingesting, normalizing, and correlating data from both worlds:
- IT data sources: Firewalls, Active Directory, email gateways, cloud applications, endpoint detection systems
- OT data sources: Historians, SCADA systems, PLCs, HMIs, industrial gateways, MES platforms, safety instrumented systems
This unified data lake enables security teams to trace attack chains that begin in IT and extend into OT. When a phishing email compromises an engineer’s laptop, Splunk can correlate that initial compromise with subsequent suspicious connections to SCADA servers, unusual PLC reprogramming attempts, or abnormal data exfiltration from historians.
Real-Time Investigation, Not Just Dashboards
Business intelligence tools show you what happened yesterday. Splunk enables you to investigate what’s happening right now—and ask follow-up questions in real time.
This investigative capability is crucial in OT environments where attacks unfold rapidly and production impacts compound by the minute. Security analysts can:
- Pivot across data sources to track lateral movement from IT systems into OT networks
- Correlate operational anomalies with security indicators to distinguish between production issues and cyber incidents
- Build custom searches on the fly without waiting for pre-built dashboard configurations
This self-service investigation model empowers the same engineers who understand production operations to also hunt for threats—creating a security-operations fusion that dramatically accelerates detection and response.
Operational Context Makes Threats Actionable
Raw security data is noise without operational context. A spike in network traffic to a PLC could indicate an attack—or it could be a scheduled firmware update. An unusual command sequence might be malicious—or it might be a new production recipe being tested.
Splunk excels at layering operational context onto security data:
- Asset relationships: Understanding which PLCs control which production lines helps prioritize incident response
- Production schedules: Correlating security events with shift changes, maintenance windows, and production runs reduces false positives
- Business impact modeling: Connecting security metrics to OEE (Overall Equipment Effectiveness), downtime costs, and production KPIs helps executive leadership understand cyber risk in business terms
This contextualization transforms OT security from a technical function into a strategic capability that directly supports operational resilience.
How bitsIO Accelerates OT Security Transformation with Splunk
Understanding the power of Splunk is one thing. Actually implementing it across complex industrial environments—spanning multiple plants, legacy systems, and fragmented data sources—is an entirely different challenge.
This is where bitsIO’s specialized expertise becomes invaluable.
Phase 1: Data Discovery and OT Security Alignment
Most organizations don’t actually know what’s connected to their industrial networks. Shadow IT and forgotten OT devices create blind spots that attackers exploit. bitsIO begins every engagement with a comprehensive data landscape assessment:
- OT asset discovery and inventory: Identifying every connected device, from modern IoT sensors to decades-old PLCs, understanding their security posture and communication patterns
- Critical data source mapping: Determining which historians, SCADA systems, and MES platforms contain the most valuable operational intelligence for security monitoring
- Security readiness assessment: Evaluating existing security controls, identifying gaps in visibility, and prioritizing quick wins versus long-term architecture improvements
The deliverable isn’t just a technical report—it’s a strategic roadmap that aligns OT security initiatives with business goals around availability, efficiency, and quality.
Phase 2: Unified OT-SIEM Implementation
With visibility gaps identified, bitsIO designs and deploys Splunk architectures specifically optimized for OT environments:
- Secure data ingestion: Implementing edge forwarders and secure data collection from OT networks without introducing new attack vectors
- Protocol normalization: Parsing industrial protocols (Modbus, DNP3, OPC-UA, CIP) into structured data that Splunk can analyze
- Common Information Model (CIM) development: Creating standardized data models aligned with ISA-95 and Unified Namespace principles, ensuring consistency across plants and systems
This isn’t a generic SIEM deployment. It’s an OT-aware architecture that respects network segmentation, minimizes bandwidth impact on production networks, and maintains the availability requirements that industrial operations demand.
Phase 3: Threat Detection and Real-Time Monitoring
With data flowing into Splunk, bitsIO develops the analytical layer that transforms raw logs into actionable security intelligence:
- OT-specific correlation searches: Detecting ransomware indicators, unusual PLC reprogramming, abnormal protocol behavior, and lateral movement patterns
- Asset-based alerting: Creating alerts tuned to the risk profile and operational context of specific assets—what’s critical for a safety system triggers different responses than anomalies in a packaging line
- Integration with existing SOC workflows: Ensuring OT security alerts flow into security operations centers alongside IT incidents, with appropriate context and prioritization
The result is a security operations capability that monitors both IT and OT environments from a single pane of glass—dramatically reducing mean time to detect and respond.
Phase 4: Operational Intelligence and Continuous Improvement
OT security monitoring isn’t a one-time project—it’s an ongoing program that evolves with your threat landscape and business operations. bitsIO provides:
- Role-based enablement training: Teaching plant engineers, IT security teams, and operations managers how to use Splunk for investigation and threat hunting
- Predictive analytics preparation: Establishing the data models and correlation logic that enable future AI-driven anomaly detection and predictive maintenance
- Governance frameworks: Building the processes, metrics, and continuous improvement cycles that sustain security maturity over time
OT Security Monitoring Best Practices
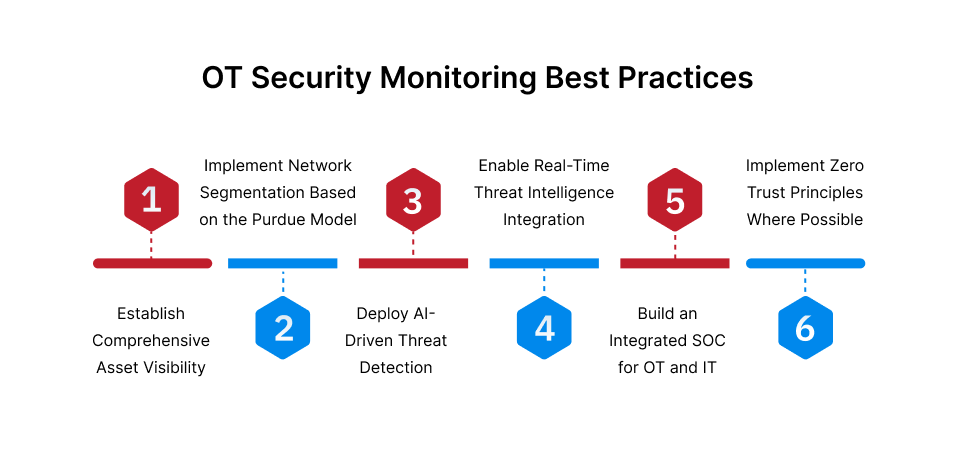
Implementing effective OT security monitoring requires more than just deploying tools. It demands a holistic approach that addresses people, processes, and technology across the entire industrial ecosystem.
1. Establish Comprehensive Asset Visibility
You can’t protect what you can’t see. OT asset management goes far beyond traditional IT asset inventories:
- Maintain living inventories: Continuously discover and catalog all connected devices, including legacy systems, shadow OT, and temporary contractor connections
- Map asset relationships: Document how assets communicate, which systems depend on which others, and what business processes each asset supports
- Track security posture: Monitor firmware versions, patch status, configuration changes, and vulnerability exposure for every asset
Splunk’s OT Security Add-on provides specialized dashboards for OT asset visibility, enabling security teams to understand their attack surface in operational terms, not just technical ones.
2. Implement Network Segmentation Based on the Purdue Model
The Purdue Enterprise Reference Architecture (PERA) often remains the gold standard for OT network segmentation:
- Level 0-1 (Process Control): Physical devices, sensors, actuators, and basic control systems—should be completely isolated
- Level 2 (Area Control): Supervisory control, HMIs, and industrial DMZ—monitored with strict firewall rules
- Level 3 (Site Operations): Manufacturing operations management, historians, MES platforms—controlled access to enterprise systems
- Level 4-5 (Enterprise): Business planning and logistics networks—standard IT security controls apply
Proper segmentation limits lateral movement. Even if attackers compromise the enterprise network, they can’t pivot directly into critical control systems without traversing monitored security zones where Splunk can detect and alert on anomalous cross-zone traffic.
3. Deploy AI-Driven Threat Detection
Modern OT security monitoring leverages artificial intelligence and machine learning to detect sophisticated threats:
- Behavioral baselining: Machine learning models establish normal operational patterns for each asset, making subtle deviations immediately visible
- Protocol anomaly detection: AI identifies unusual commands, unauthorized protocol behavior, and malformed industrial traffic that signature-based detection would miss
- Automated correlation: AI accelerates the correlation of indicators across IT and OT environments, reducing alert fatigue and highlighting the threats that matter most
Splunk AI Toolkit enables organizations to build custom anomaly detection models tuned to their specific operational environments.
4. Enable Real-Time Threat Intelligence Integration
OT threats evolve constantly. Static security controls quickly become obsolete:
- Subscribe to OT-specific threat intelligence feeds: Industrial threat intelligence from providers like CyberVision, Dragos, Claroty, and Nozomi provides early warning of vulnerabilities and attack campaigns targeting ICS
- Correlate threat intel with internal data: Automatically match indicators of compromise (IOCs) against your Splunk data to identify if your environment has been targeted
- Operationalize threat hunting: Use threat intelligence to proactively hunt for adversary tactics, techniques, and procedures (TTPs) within your OT environment before incidents occur
5. Build an Integrated SOC for OT and IT
The artificial separation between IT security operations and OT security operations creates dangerous blind spots. Modern industrial security requires:
- Unified security operations centers: One team monitoring both IT and OT, with specialized training in industrial protocols and operational risk
- Common incident response playbooks: Processes that account for the unique constraints of OT environments (where quarantining a device might halt production)
- Executive-level visibility: Dashboards that translate security metrics into business impact—downtime risk, production loss, safety implications
bitsIO’s Industrial Data Intelligence Services specifically address this integration challenge, creating role-based views in Splunk that serve everyone from plant floor operators to CISOs to board members.
6. Implement Zero Trust Principles Where Possible
While full Zero Trust implementation in OT faces technical constraints, key principles can significantly improve security:
- Least privilege access: Strictly limit who can access OT systems and what actions they can perform
- Multi-factor authentication: Require MFA for all remote access to OT networks and critical control systems
- Continuous verification: Never trust, always verify—even for internal network connections
- Microsegmentation: Go beyond Purdue zones to isolate individual critical assets where possible
Splunk monitors these Zero Trust controls, alerting when authentication anomalies, privilege escalations, or policy violations occur.
Building Resilience in the Age of Persistent Threats
The journey from ransomware vulnerability to operational resilience isn’t a single project—it’s a continuous evolution of capabilities, culture, and strategic investment.
Modern ICS environments face threats that are sophisticated, persistent, and increasingly targeted. Traditional security approaches built for IT networks fall short when applied to operational technology, where uptime is measured in safety and economic impact, not just data protection.
The organizations that will thrive aren’t necessarily the ones with the biggest security budgets. They’re the ones that:
- Unify visibility across IT and OT using platforms like Splunk that understand both domains
- Empower their people with the training and tools to investigate threats in real time
- Embed security into operations rather than treating it as a separate function
- Partner with specialists who bring deep expertise in both industrial operations and cybersecurity
bitsIO’s Industrial Data Intelligence Services provide exactly this combination—technical excellence in Splunk implementation, operational understanding of industrial environments, and strategic guidance that aligns cybersecurity investments with business outcomes.
The threat landscape won’t get easier. Ransomware groups continue to evolve. Nation-state actors increasingly target critical infrastructure. The attack surface expands as Industry 4.0 initiatives connect more devices to more networks.
But with the right platform, the right implementation partner, and the right approach to OT security monitoring, your organization can move from reactive defense to proactive resilience.
Ready to Transform Your OT Security Posture?
Don’t wait for a ransomware incident to discover gaps in your OT security monitoring capabilities. The cost of prevention is always lower than the cost of response—and infinitely lower than the cost of unplanned downtime.
Book a free consultation with bitsIO experts to discuss:
- Your current OT security visibility and gaps
- How Splunk can unify monitoring across your IT and OT environments
- A roadmap for building resilient industrial security operations
- Strategies tailored to your specific industry and operational constraints
Your industrial operations keep the world running. Let bitsIO and Splunk help you keep them secure.
Frequently Asked Questions















