Summarize the Content of the Blog
Key Takeaways
Splunk SOAR reduces alert fatigue by filtering out false positives and surfacing only high-priority incidents.
Automating response actions enables faster detection and containment of threats, such as fraudulent payments, without expanding headcount.
Real-time evidence gathering supports audit readiness and helps maintain compliance with standards like PCI-DSS, SOX, and GDPR.
SOAR integrates seamlessly with existing tools, eliminating workflow silos and unifying detection, triage, and response.
Automated playbooks reduce manual workloads, boost analyst morale, and improve overall SOC efficiency.
The effectiveness of Splunk SOAR depends on how well it's implemented, and strategic partners like bitsIO ensure long-term value and resilience.
Security Operations Centers (SOCs) today aren’t just battling external threats; they’re overwhelmed with alert noise, disconnected tools, and mounting compliance pressure. According to the World Economic Forum, cyber risks have increased in 72% of organizations over the past year, with 63% citing rapidly evolving threats as the top barrier to achieving cyber-resilience.
The Splunk State of Security 2025 findings add more clarity: 46% of security leaders spend more time maintaining tools than on threat mitigation, and more than half of their SOCs have to deal with too many alerts, false positives, and a lack of context for understanding alerts.
Regulatory frameworks like PCI-DSS, SOX, and GDPR only add to the pressure, demanding faster, auditable response processes. And despite the widespread use of Splunk SIEM, many SOCs still rely on manual triage and ticketing, which slows down threat response.
Why Alert Fatigue Is a Strategic Risk
When critical alerts are buried under routine or redundant notifications, real threats like fraudulent payment activity slip through unnoticed. The consequences aren’t limited to delayed investigations, but they often extend to financial loss, regulatory exposure, and reputational damage. A single missed incident could trigger legal scrutiny, customer churn, or even board-level accountability.
This fatigue also creates internal risk. Teams burn out, morale drops, and skilled analysts either disengage or move on to other opportunities. The longer the noise persists, the more challenging it becomes to maintain a mature and responsive SOC.
In this environment, simply having the right tools isn’t enough. SOCs require a more innovative approach to handling volume, one that filters out the noise and surfaces only what truly matters.
How to Reduce Alert Fatigue in SOC Environments
If alert fatigue is a strategic risk, then reducing it must become a strategic priority. Most Security Operations Centers rely on a mix of detection tools, each firing alerts independently. The result? Thousands of notifications are sent daily, many of which are low-priority or duplicates. Analysts end up chasing noise instead of threats, wasting time, delaying response, and increasing the risk of missing something critical.
Splunk SOAR addresses this by acting as the orchestration layer between your existing tools. It connects to SIEMs, EDRs, threat intelligence platforms, and more, correlating alerts across systems, enriching them with relevant context, and using SOAR playbooks to filter out false positives. Only the most pertinent alerts reach human analysts.
This is an operational upgrade. By removing repetitive triage work and enabling high-fidelity detection, Splunk SOAR helps reduce analyst burnout, improve mean time to detection, and enhance Splunk's threat response capabilities. And because it integrates directly with Splunk SIEM, the entire alert lifecycle is traceable and consistent.
SOAR Implementation in Splunk: What Makes it Different?
Security teams today need intelligent, scalable response systems that integrate deeply with existing workflows. That’s the core strength of SOAR implementation in Splunk.
Instead of adding complexity, Splunk SOAR connects your SIEM, threat intel feeds, ticketing systems, and enforcement tools. It extends Splunk’s detection capabilities into orchestrated, automated action, without losing visibility, control, or auditability.
Unlike generic automation platforms, Splunk SOAR natively integrates with Splunk Enterprise Security. This allows for seamless event ingestion, centralized case management, and enrichment at the point of triage. Security teams can filter and prioritize incidents in real time, using enriched data from multiple systems, including EDRs, firewalls, IAM tools, and sandboxing solutions.
With over 350 integrations and 2,800 prebuilt actions, Splunk SOAR eliminates the need for custom scripting or manual API calls for faster deployment and operational agility.
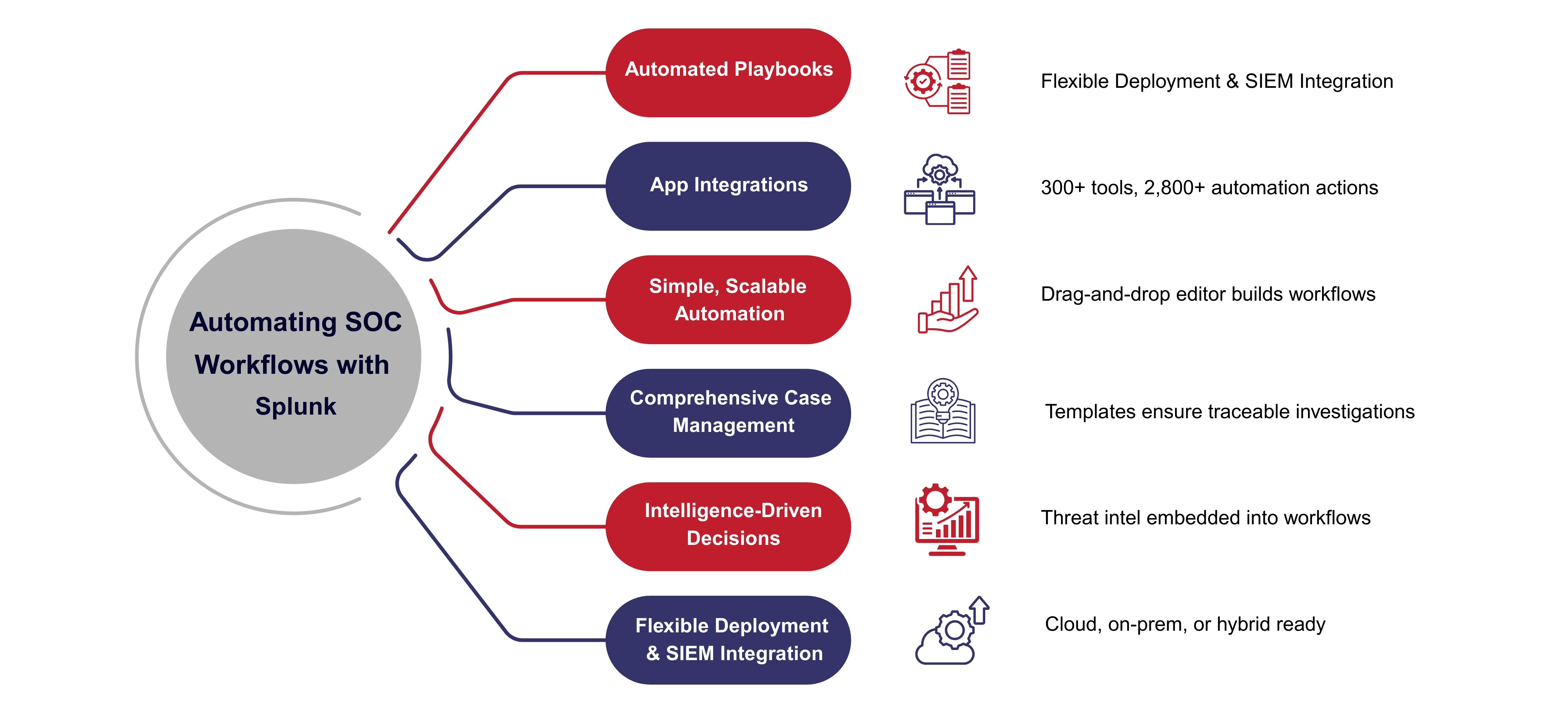
Automating SOC Workflows with Splunk
At the core of this automation capability are Splunk SOAR playbooks. These are visual workflows that automate and standardize response actions, allowing teams to safely build, test, and deploy repeatable processes with minimal risk.
Beyond playbooks, the platform includes a set of capabilities that work together to support end-to-end security operations:
1. Automated Playbooks
Splunk SOAR allows teams to execute response actions across security and IT tools within seconds. Rather than spending hours on manual triage or investigation, analysts can deploy a library of pre-built playbooks to handle use cases such as phishing, malware containment, access validation, and more. This reduces time-to-respond without sacrificing accuracy.
2. App Integrations
With over 300 supported third-party tools and more than 2,800 prebuilt automation actions, Splunk SOAR integrates directly into your existing environment. Teams can coordinate complex workflows without needing to replace or reconfigure their security stack. This compatibility ensures faster time to value and easier deployment.
3. Simple, Scalable automation
Whether you’re new to automation or have a mature process in place, Splunk SOAR’s Visual Playbook Editor makes it easy to create custom workflows. Using a drag-and-drop interface and modular code blocks, teams can build automation logic that is easy to understand and maintain. This lowers the learning curve and empowers security staff at all levels to contribute.
4. Comprehensive Case Management
Every alert or incident can be managed using built-in case templates or customized workflows. Splunk SOAR provides structured task segmentation, assignment tracking, and detailed documentation tools. This ensures a collaborative and traceable investigation process that aligns with internal policies and external regulatory standards.
5. Intelligence-Driven Decisions
Splunk SOAR’s investigation panel provides analysts with a unified view of incoming threats, so they can determine where to act first. With threat intelligence data built directly into the workflow, teams can access real-time insights, reputation scores, and behavioral indicators. These inputs originate from the Splunk Threat Research Team and help analysts stay one step ahead of attackers.
6. Flexible Deployment and SIEM Integration
Splunk SOAR can be deployed in the cloud, on-premises, or as a hybrid solution. When combined with Splunk Enterprise Security, it offers a fully integrated security operations platform. Analysts can move from detection to response without switching tools, and every action is logged for compliance and audit purposes.
The impact of this automation is already visible across industries.
Real-World Splunk SOAR Use Cases for Security Teams
Splunk SOAR use cases for security teams across industries show measurable gains in response speed, efficiency, and analyst morale. Here’s a case study demonstrating how automating SOC workflows with Splunk can solve persistent operational bottlenecks.
Core Principles for Building Resilient SOAR Playbooks
Building effective SOAR playbooks involves designing workflows that adapt over time, align with compliance mandates, and accurately reflect how your security team operates.
Strong playbooks follow a few core principles:
- Trigger Specificity: Effective playbooks start with precise event triggers, such as phishing emails, unauthorized access attempts, or risky file uploads. This ensures they only activate when needed.
- Data Enrichment: Integrating threat intelligence, user context, asset sensitivity, and geolocation helps analysts to make more informed decisions without switching between tools.
- Conditional Logic: Playbooks should adapt based on context, such as alert severity, asset value, or user risk level, so that responses are appropriate, prioritized, and efficient.
- Audit-Ready Actions: Every step, from triage to containment, should be logged, timestamped, and traceable to meet standards like PCI-DSS, SOX, and GDPR.
However, these workflows must evolve. As threats change and your SOC matures, playbooks should be versioned, tested in sandbox environments, and adjusted based on feedback.
The goal isn’t to replace human judgment but to reduce noise and let analysts apply their expertise where it counts. That’s where implementation makes all the difference.
Why bitsIO Is the Right Partner for SOAR Implementation in Splunk
The value of Splunk SOAR lies in how well it’s deployed. That’s why enterprises trust bitsIO to implement, optimize, and manage their SOAR environments end-to-end.
By designing risk-aligned playbooks and automating real-world workflows, bitsIO helps turn reactive security operations into proactive defence strategies. Pre-built libraries, proven frameworks, and sandbox testing ensure safe, confident deployments, while training empowers internal teams to operate and adapt independently.
Beyond go-live, bitsIO delivers ongoing optimization and strategic guidance, helping SOCs not only respond faster but also anticipate and stay ahead of evolving threats. The result: a resilient, compliant, and scalable security foundation.
Conclusion
What sets Splunk SOAR apart is its focus on end-to-end lifecycle management. From alert ingestion and enrichment to automated response and compliance logging, every stage of the process is unified and streamlined. This tight coupling means SOC analysts don’t have to swivel-chair between platforms, duplicate data, or question the source of truth. And critically, it supports full audit trails, making it easier to demonstrate due diligence for standards like PCI-DSS, SOX, and GDPR.
As a trusted Splunk partner, bitsIO doesn’t just deploy SOAR; we build the strategy, design resilient playbooks, train internal teams, and support continuous optimization. Whether you’re aiming to reduce alert fatigue, respond more quickly to fraud, or establish a mature automation framework, bitsIO ensures you get there with confidence.















