Our blog
Installation Guide for Supporting Add On for MITRE ATT&CK®

Supporting Add On for MITRE ATT&CK®
This app provides a method to ingest MITRE ATT&CK tactics, techniques, and subtechniques into Splunk events. The app contains a mitre_techniques KVStore with the metadata provided from ATT&CK to help enrich alerts and ES Correlations without needing to navigate back to the ATT&CK website.
Sourcetypes
| Source type | Description |
| mitre:techniques | ATT&CK tactic and techniques as defined https://raw.githubusercontent.com/mitre/cti/master/enterprise-attack/enterprise-attack.json |
| mitre:subtechniques | ATT&CK sub techniques as defined https://raw.githubusercontent.com/mitre/cti/subtechniques/enterprise-attack/enterprise-attack.json |
Hardware and software requirements for SA-mitre
Outbound internet access to the following URLs:
https://raw.githubusercontent.com/mitre/cti/master/enterprise-attack/enterprise-attack.json
https://raw.githubusercontent.com/mitre/cti/subtechniques/enterprise-attack/enterprise-attack.json
Install SA-mitre
Where to install this add-on
IMPORTANT:
Standalone Search Head (will not work on Search Head Cluster)
Direct internet connection required (no proxy)
This table provides a reference for installing this specific add-on to a distributed deployment of the Splunk platform.
| Splunk instance type | Supported | Required | Comments |
| Search Heads | Yes | Yes | Install this add-on to all search heads where MITRE ATT&CK knowledge management is required. |
| Indexers | No | No | KVStore replication to indexers does not require this to be deployed directly on indexers. |
| Heavy Forwarders | No | No | This add-on does not contain any knowledge objects needed on forwarding tier. |
| Universal Forwarders | No | No | This add-on does not contain any knowledge objects needed on forwarding tier. |
Configure SA-mitre
- Install SA-mitre on the search head(s) you would like the enriched ATT&CK data on.
- Navigate to the SA-mitre app > Inputs tab.
- Create new input > mitre_technique
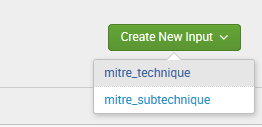
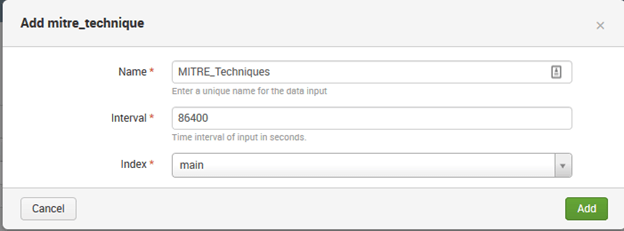
- Provide a name for the modular input, frequency you want to download and ingest the framework data and index you want to save the data too.
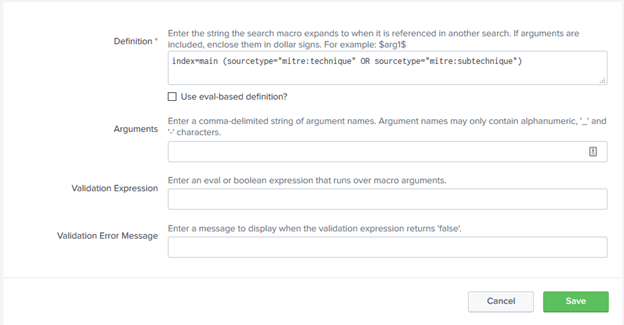
- Update indexmitre macro with correct index and sourcetype if you are not using index=main. Settings > Advanced Search > Search Macros > indexmitre
- Once data has been indexed, run the mitre_techniques Lookup Gen to populate the KVStore.
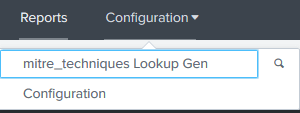
- Optional – Schedule the mitre_techniques Lookup Gen saved search to run on a daily/weekly schedule based on your Interval defined in the input.
How to use mitre_techniques KVStore
Given a MITRE Tactic or Technique you can use this KVStore to enrich events with contextual data.
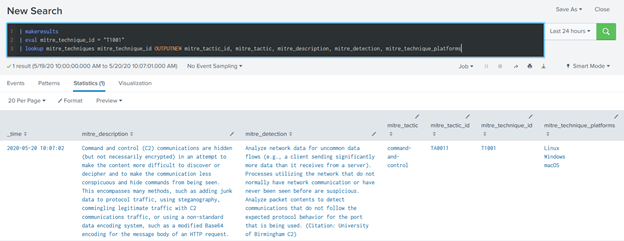
| makeresults | eval mitre_technique_id = "T1001" | lookup mitre_techniques mitre_technique_id OUTPUTNEW
Troubleshooting
Modular input logs can be found by searching:
index=_internal sourcetype="samitre:log"
Appendix A: mitre_techniques KVStore Schema
| Field name | Data type | Description |
| mitre_technique_id | string | The MITRE ATT&CK technique ID such as T1001. |
| mitre_technique | string | The MITRE ATT&CK technique name such as Data Obfuscation. |
| mitre_tactic_id | string | The MITRE ATT&CK tactic ID such as TA0001. |
| mitre_tactic | string | The MITRE ATT&CK tactic name such as Initial Access. |
| mitre_description | string | The MITRE ATT&CK technique description. |
| mitre_url | string | The MITRE ATT&CK technique URL for additional reference material. |
| mitre_detection | string | The MITRE ATT&CK technique detection information. |
| mitre_technique_platforms | string | The MITRE ATT&CK technique platforms such as windows, linux, or mac. |
| mitre_threat_group_name | string | The MITRE ATT&CK technique associated group names such as APT19. |
| mitre_threat_group_aliases | string | The MITRE ATT&CK associated group aliases. |
| mitre_threat_group_url | string | The MITRE ATT&CK group URL for additional reference material. |
| mitre_threat_group_id | string | The MITRE ATT&CK group ID such as G0073. |
| mitre_software_name | string | Associated software name such as Mimikatz. |
| mitre_software_type | string | Associated software type such as Tool. |
| mitre_software_platform | string | Associated software platforms such as windows, linux or mac. |
| mitre_software_url | string | Associated software URL for additional reference material. |
Search Here
Latest Posts


