Our blog
Maximizing Efficiency: Remediation as a Service with Splunk SOAR


The digital landscape is under constant siege, with security threats evolving faster than ever. In this high-stakes environment, efficient incident response is the name of the game. Splunk SOAR, paired with the power of ServiceNow ticketing, presents a formidable duo, but unlocking their full potential requires strategic orchestration.
This blog post dives deep into threat analysis and ticket management playbooks, your secret weapon for maximizing efficiency in Splunk SOAR and ServiceNow. Know what RaaS is, why it is necessary and understand its conceptual structure.
Playbook 1: Threat Analysis & Creating ServiceNow Incident Ticket - Updating Custom List on SOAR using the Automation Playbook.
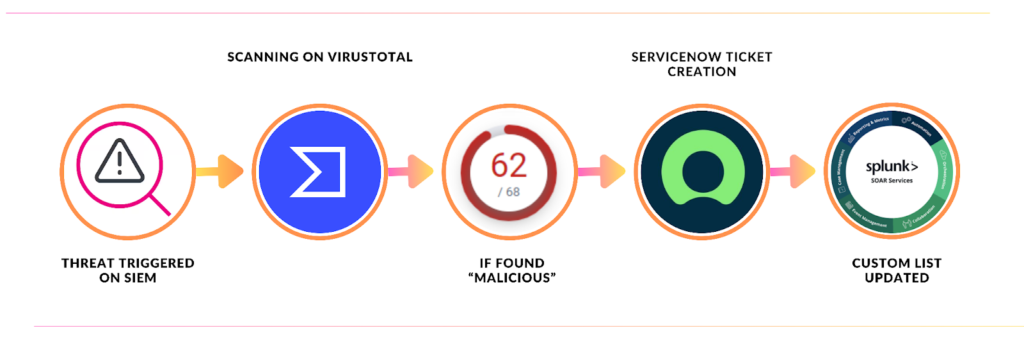
Focus: This playbook seamlessly combines initial threat analysis, ServiceNow ticket creation, and automatic list population for efficient incident tracking and management.
Steps:
- Threat Analysis: Upon receiving an alert, analysts delve into the associated artifacts to assess potential malicious activity.
- Automated Ticket Creation: Based on the analysis, the playbook automatically opens a ServiceNow incident ticket populated with relevant details from the alert. This includes information like source, severity, timestamp, and initial observations.
- Custom List Creation: Simultaneously, Splunk SOAR builds a dedicated custom list for the incident, capturing vital information like “Ticket Number,” “Ticket Opened at,” “Ticket Status,” and “Ticket Description.”
- Centralized Tracking: This custom list serves as a single source of truth for the incident, allowing analysts to monitor progress, update details, and trigger additional actions efficiently.
Optional Automation: You can further enhance the playbook by configuring it to:
- Trigger additional investigations based on specific threat attributes.
- Assign the ticket to relevant security teams based on threat classification.
- Send notifications to analysts or stakeholders with key updates.
Benefits:
- Streamlined incident response: Automate ticket creation and data population, saving time and reducing manual effort.
- Centralized information: Maintain a single, up-to-date view of the incident across ServiceNow and Splunk SOAR.
- Efficient tracking and management: Easily monitor progress, prioritize threats, and take targeted actions.
- Improved collaboration: Facilitate communication and coordination among analysts with the centralized custom list.
Playbook 2: Automation Playbook to Update the Status of Ticket(s) on Custom List on Splunk SOAR
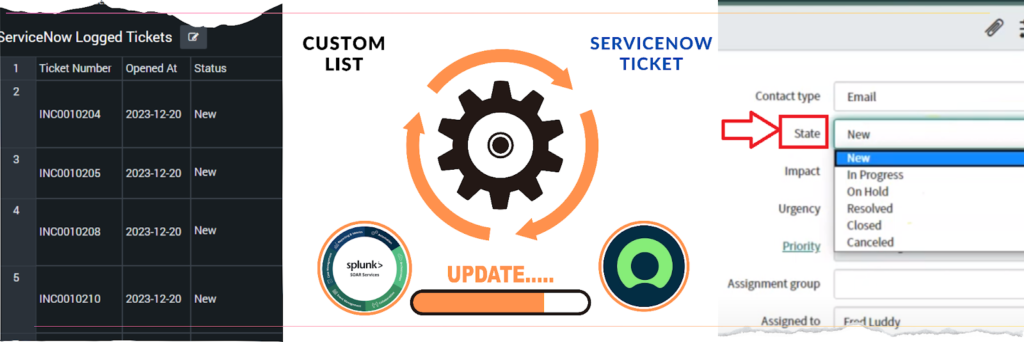
Focus: This playbook effortlessly maintains real-time accuracy of the custom list by syncing ticket status changes from ServiceNow to Splunk SOAR, ensuring a unified view of incident progress.
Steps:
- Continuous Monitoring: The playbook establishes a persistent connection with ServiceNow, vigilantly watching for updates to incident ticket statuses.
- Seamless Synchronization: Upon detecting a status change (e.g., resolved, closed, escalated), the playbook promptly retrieves the updated information.
- Automatic List Refresh: It then seamlessly reflects these changes on the corresponding entries within the custom list on Splunk SOAR, ensuring alignment with ServiceNow.
Triggering Additional Actions: Optionally, you can configure this playbook to:
- Send notifications to analysts or stakeholders when critical tickets change status.
- Close related investigations or tasks in Splunk SOAR based on the updated status.
- Trigger further automation actions or playbooks based on specific status triggers.
Benefits:
- Enhanced Visibility: Maintain a real-time overview of incident progress and priorities, enabling informed decision-making.
- Reduced Manual Effort: Eliminate the need for analysts to manually update ticket statuses, freeing up time for more strategic tasks.
- Improved Accuracy: Mitigate the risk of errors or inconsistencies that can arise from manual updates, ensuring data integrity.
- Accelerated Response: Enable analysts to respond quickly and decisively to evolving incidents based on accurate status information.
- Streamlined Workflows: Foster a more efficient and agile incident response process by automating status updates and triggering downstream actions.
Playbook 3: Automation Playbook to Purge Closed Status Tickets from Custom List and Notify Analysts
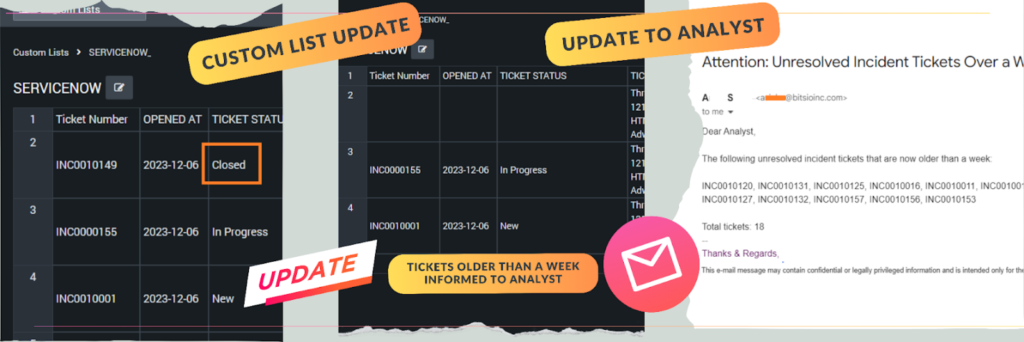
Focus: This playbook maintains a clean and efficient custom list by automatically removing resolved tickets and proactively notifying analysts about potential action items.
Steps:
- Closed Ticket Identification: The playbook periodically scans the custom list in Splunk SOAR, searching for entries with a status of “closed.”
- Automatic Purge: Upon identifying closed tickets, it efficiently removes them from the list, preventing clutter and ensuring focus on active threats.
- Stale Ticket Notifications: It also proactively examines open tickets, pinpointing those with a status of “new,” “on-hold,” or “in progress” that have been stagnant for over 7 days.
- Alerting Analysts: For these stale tickets, the playbook sends targeted notifications to analysts, highlighting potential action items or escalation needs.
Customizable Notifications: You can further tailor this playbook to:
- Send notifications to specific analysts or teams based on ticket ownership or priority.
- Include additional context or data within the notifications to aid decision-making.
- Trigger further actions or playbooks based on stale ticket criteria.
Benefits:
- Improved List Maintainability: Keep the custom list organized and focused on active threats, enhancing its usability for analysts.
- Reduced Clutter: Eliminate irrelevant information, making it easier to visualize and prioritize ongoing incidents.
- Prompt Action on Stale Tickets: Prevent tickets from lingering in limbo, ensuring timely resolution and reducing potential risks.
- Enhanced Analyst Awareness: Bring attention to potential bottlenecks or areas requiring escalation, fostering proactive incident management.
- Streamlined Workflows: Automate ticket management tasks, freeing up analyst time for more strategic analysis and response.
Conclusion:
Splunk SOAR’s trio of playbooks for threat analysis and ticket management demonstrates a holistic approach to incident response. By seamlessly integrating with ServiceNow and automating processes from ticket creation to status updates and purging closed cases, Splunk SOAR empowers organizations to respond to cyber threats swiftly and efficiently. In an era where time is of the essence, these playbooks stand as indispensable tools for cybersecurity teams striving to stay ahead of adversaries.
Search Here
Latest Posts


